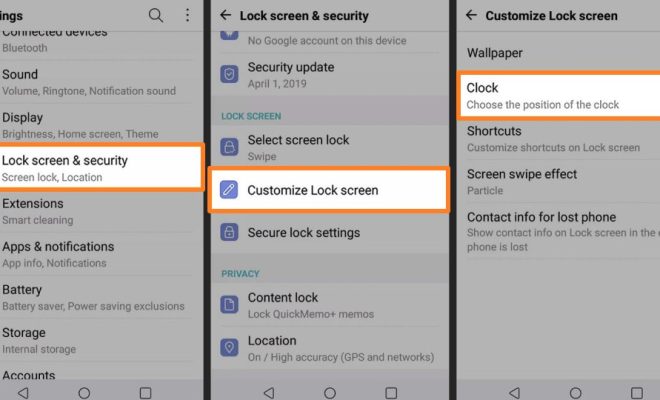
How Your Phone Can Be Hacked Remotely and What You Can Do to Stop It

As more and more of our lives are stored on our phones, it’s becoming increasingly important to be aware of the possibility of remote hacking. Remote access to a phone can give hackers access to sensitive information such as your login credentials, bank details, and even your location. In this article, we’ll discuss how your phone can be remotely hacked and what you can do to stop it.
First, it’s important to understand how remote hacking works. Hackers can gain access to your phone through various methods, including spear phishing, malicious software or apps, man-in-the-middle attacks, and through vulnerabilities in your phone’s operating system or network. Once they have gained access, they can monitor your activity, steal data, and even control your phone remotely.
Now, let’s talk about what you can do to protect yourself from remote hacking. The following tips can help keep your phone secure:
1. Use strong passwords: One of the easiest ways for a hacker to gain access to your phone is by guessing your password. Make sure your password is strong, contains a mix of numbers, letters, and special characters, and is unique to your phone. Never use the same password across multiple accounts.
2. Keep your phone updated: Always make sure your phone’s operating system and apps are up to date. Updates often include security patches that fix vulnerabilities that could be exploited by hackers.
3. Install anti-malware software: Anti-malware software can help protect your phone from viruses, trojans, and other types of malicious software that hackers use to gain control of your device.
4. Be careful when connecting to public Wi-Fi: Public Wi-Fi is a common target for hackers. Make sure you’re connected to a secure network and use a virtual private network (VPN) to protect your data when using public Wi-Fi.
5. Be wary of suspicious links and downloads: Don’t click on links or download files from unknown sources. Hackers often use phishing emails and social engineering tactics to trick users into installing malware on their devices.
6. Enable two-factor authentication: Two-factor authentication adds an extra layer of security to your accounts. It requires you to enter a password and an additional verification method, such as a fingerprint or a code sent to your phone.