What Is a Root Certificate and How Can It Be Used to Spy on You?
As more and more people rely on the internet for their daily activities, the importance of online security has become paramount. One of the most important aspects of online security is the use of SSL (Secure Sockets Layer) certificates. SSL certificates provide a secure connection between a user’s computer and a website’s server, ensuring that any sensitive data exchanged between them cannot be intercepted by third parties.
However, not all SSL certificates are created equal, and some can be used to spy on users. This is where root certificates come into play.
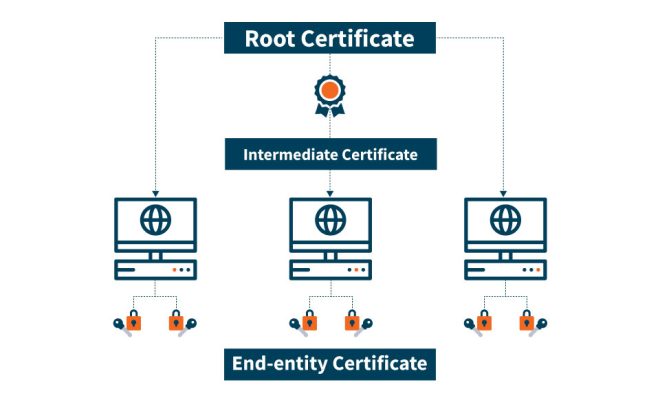
A root certificate is a digital certificate issued by a trusted root certificate authority (CA). Root CAs are responsible for verifying the identity of organizations and issuing SSL certificates to websites. Essentially, a root certificate is the digital equivalent of a passport or driver’s license, providing verification of a website’s identity.
The problem with root certificates is that they can be used for surveillance. If a government or other entity wants to spy on internet traffic, they can create their own root certificate and distribute it to users. When a user visits a website with an SSL certificate issued by the rogue root CA, their traffic can be intercepted and decrypted, allowing the spy to monitor their online activity.
This type of surveillance is commonly known as a “man-in-the-middle” attack. In this scenario, the spy intercepts all communication between the user and the website, allowing them to see everything the user is doing online, including usernames, passwords, and other sensitive information.
One high-profile example of this type of surveillance is the case of Superfish. In 2015, Lenovo, a Chinese technology company, pre-installed a root certificate on some of its laptops that allowed Superfish, a third-party software, to monitor users’ internet activity. This was done without the users’ knowledge or consent, and it was quickly discovered by security researchers.
To protect yourself from root certificate surveillance, it’s important to use SSL certificates from reputable CAs and to keep your internet security software up-to-date. Additionally, you can check your list of trusted root certificates on your computer to ensure that only trusted CAs are included.
In conclusion, root certificates play a critical role in online security, but they can also be used to spy on users. As internet usage continues to grow, it’s essential that users stay vigilant and take steps to protect themselves from online surveillance.