Everything You Need to Know About the Twofish Encryption Algorithm
Encryption algorithms are a crucial part of modern technology. They are used to protect sensitive information across the internet, on cloud servers, and even on local devices. One of the most secure encryption algorithms currently available is the Twofish algorithm. In this article, we will explore everything you need to know about the Twofish encryption algorithm.
What is the Twofish Encryption Algorithm?
Twofish is a symmetric key block cipher encryption algorithm, which means that the same key is used for both encryption and decryption. It was developed in 1998 by Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, and Niels Ferguson. Twofish was designed to be a safe, fast, and flexible encryption algorithm.
How Does Twofish Work?
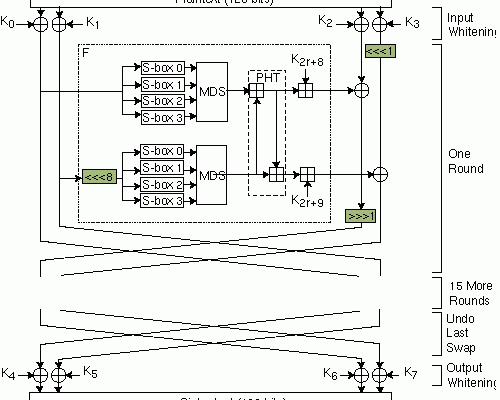
The Twofish encryption algorithm operates on 128-bit blocks of data. The key size can be up to 256 bits, making it a powerful encryption algorithm that is difficult to crack. The encryption process involves the use of the round function, which processes the input data using four different block operations. These operations are mixed in a highly complex way, making the Twofish encryption algorithm exceptionally difficult to reverse engineer.
Twofish is a Feistel network, meaning that it divides the input data into two halves and applies a series of operations to each half. The operations are repeated for a specific number of rounds, which depends on the size of the key. The decryption process undoes the encryption process by using the same key and applying the inverse operations in reverse order.
What are the Benefits of Using Twofish Encryption?
1. Security: The Twofish encryption algorithm is widely regarded as one of the most secure encryption algorithms currently available. It can protect against brute force and other types of attack.
2. Speed: Twofish is a fast encryption algorithm that can quickly encrypt and decrypt large amounts of data. It is faster than other encryption algorithms like AES.
3. Flexibility: Twofish can be used in a variety of applications, such as file encryption, network security, and secure communication protocols.
4. Simplicity: Twofish is a simple encryption algorithm that is easy to understand and implement.
Conclusion
The Twofish encryption algorithm is a powerful and highly secure encryption algorithm that can protect sensitive data from prying eyes. It is a fast and flexible encryption algorithm that can be used in a variety of applications, providing peace of mind for businesses and individuals alike. Overall, the Twofish encryption algorithm is an excellent choice for those looking for a reliable and secure encryption algorithm.